I have a Raspberry Pi which is located in a remote place. The only communication methods can be established is to use 4G LTE cellular networks with no static IP address provided. Can I reach my Raspberry Pi from my computer or from my smartphone, also assuming both devices don’t have static IP addresses ? Absolutely. As long as there is a SSH server which has a static IP address that can be accessed from both sides, I can retrieve or send data from my computer to Raspberry Pi.
Raspberry Pi needs to establish a route using reverse tunnel or known as a remote forwarding. It routes a traffic to local machine which in this case is “my computer” or other destinations. Since my computer doesn’t have a static IP address, the traffic can be routed to SSH server which has a static IP address.
For all connections here, we use private and public keys so we will not be required to enter password everytime we connect to the server.
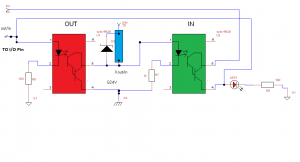
SSH Reverse Tunnel or Remote Forwarding.
On Raspberry pi we will enter the following:
ssh -v -i /home/pi/serverkey -R 5112:localhost:22 -p 22 myaccount@107.175.72.199
My user id on ssh server is myaccount. For connecting to the server , it has a port 22 for ssh and an IP address 107.175.72.199. Serverkey which is stored in directory /home/pi is a private key which has to match a ssh server public key.
Here is the important part:
-R 5112:localhost:22
-R means remote forwarding. It will route port 22 on Raspberry pi to destination port 5112 which is located on ssh server.
-i identify file.
-v verbose.
SSH Tunnel or Local Forwarding.
On my computer which has own a ssh server , I can access destination port 5112 that will route the traffic to Raspberry Pi port 22 using following command:
ssh -v -i /home/mycomputer/serverkey -L 5112:localhost:22 -p 22 myaccount@107.175.72.199
I can also connect the Raspberry Pi using my phone with a SSH client installed.
After connection established and able to login to 107.175.72.199 server, the last step is to login to Raspberry SSH terminal:
ssh -i pikey -p 5112 pi@localhost
pikey is an identity file for a private key that must match Raspberry pi public key.




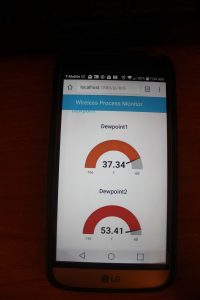
 Picture A.
Picture A. Picture B.
Picture B.
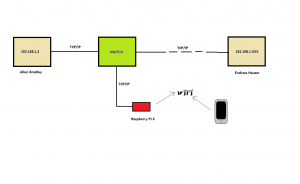
 Picture D.
Picture D.